What Is EDR? Understanding Endpoint Detection and Response
Endpoint Detection and Response (EDR) is a critical cybersecurity capability designed to provide visibility, detection, and response across endpoints in modern, distributed environments. As organizations adopt remote work and rely on interconnected devices, traditional antivirus solutions alone are no longer sufficient.
Why Endpoint Security Has Become More Challenging
Modern organizations operate with laptops, desktops, servers, and mobile devices spread across different locations and networks. Monitoring each endpoint individually for malware, suspicious behavior, or compromise is extremely difficult using manual methods or legacy tools.
This is where Endpoint Detection and Response (EDR) becomes essential. EDR centralizes endpoint visibility by collecting telemetry data and providing tools to analyze, investigate, and respond to threats.
What Is EDR?
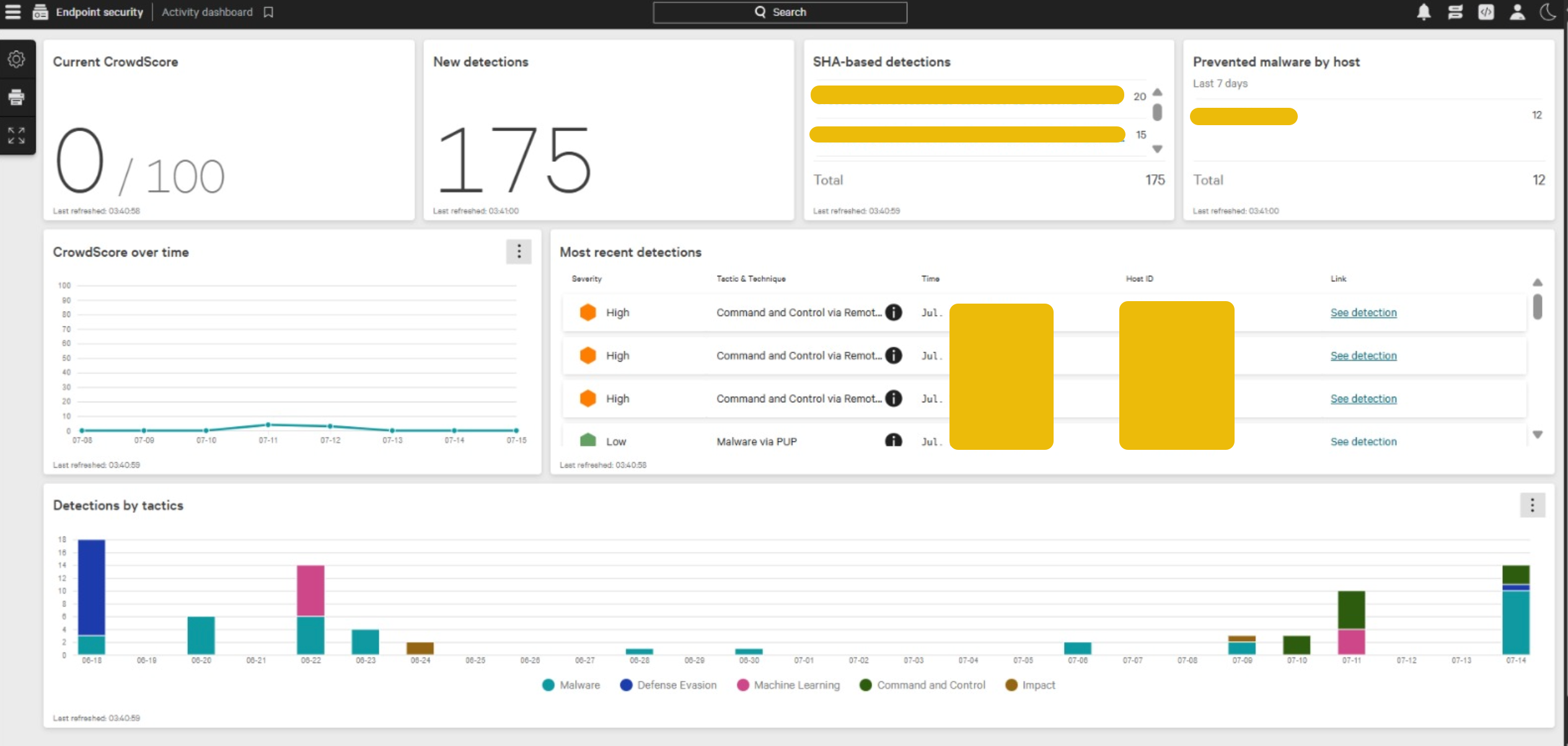
Endpoint Detection and Response is a security solution that continuously monitors endpoints by collecting telemetry data and analyzing it to identify malicious or suspicious activity. EDR platforms provide security teams with detailed visibility into what is happening on endpoints and the ability to respond quickly when threats are detected.
At its core, EDR focuses on three key capabilities:
- Visibility – understanding what is happening on each endpoint
- Detection – identifying malicious or suspicious behavior
- Response – taking action to contain and remediate threats
How EDR Differs from Traditional Antivirus
Traditional antivirus (AV) solutions primarily rely on signature-based detection. They compare files and activities against a database of known threats. While this approach can stop known malware, it struggles when threats disguise themselves as legitimate processes or use previously unseen techniques.
EDR excels where antivirus falls short. Instead of only checking files, EDR analyzes behavior and context. It uses detection rules, behavioral analysis, and machine learning to distinguish between legitimate and malicious activity, even when a process initially appears normal.
How EDR Works
EDR solutions operate by deploying lightweight agents (also called sensors) on endpoints. These agents continuously collect telemetry data and send it to a centralized EDR console for analysis.
Common types of telemetry collected include:
- Process and command execution
- Network communications
- File and folder modifications
- Registry changes
- User and system activity
Detection Techniques Used by EDR
EDR platforms use multiple detection techniques to identify threats:
- Behavioral analysis to detect abnormal activity
- Indicators of Compromise (IOC) matching
- Machine learning algorithms
- MITRE ATT&CK framework mapping to understand attacker behavior
This layered detection approach allows EDR to detect advanced threats that bypass traditional defenses.
Response Capabilities in EDR
Detection alone is not enough. One of the most powerful aspects of EDR is its response capability. Once a threat is identified, security teams can take immediate action.
Common response actions include:
- Isolating the affected host from the network
- Terminating malicious processes
- Quarantining or deleting malicious files
- Remote access to endpoints for investigation and remediation
EDR vs SIEM
While EDR focuses on endpoints, a Security Information and Event Management (SIEM) system aggregates and correlates data from multiple security tools. A SIEM may ingest logs from EDR platforms, firewalls, network monitoring tools, and other sources.
In this sense, EDR often acts as a critical data source within a broader security ecosystem rather than a replacement for SIEM.
Personal Takeaway
Learning about EDR highlighted why modern security strategies must go beyond prevention. Visibility and response are essential, especially when dealing with sophisticated threats that evade traditional controls.
As a next step, I plan to explore EDR solutions hands-on by testing them on my own system. This practical approach will help deepen my understanding of how endpoint telemetry, detection, and response work in real-world scenarios.



No comments yet.